Requirements for the product integration
In order to successfully integrate your product into the STACKIT Marketplace, certain requirements must be met. This chapter describes the requirements in terms of structural, quality and security requirements that are necessary for integration and listing.
Prerequisites
Section titled “Prerequisites”- You have a STACKIT user account: Create a user account
- You have the following
project.writerole assigned: Assign a role to a user account - You are member of an active organization: Create a customer account
- You have created a service account for API access: Create a service account
- The service account has the editor role assigned: Assign roles to a service account
- You have created a key pair for this service account: Create a service account key
Quality and safety requirements
Section titled “Quality and safety requirements”Every product on the STACKIT Marketplace must meet the following requirements. The STACKIT Marketplace integration team continuously checks whether all product requirements are met. If a product violates a requirement, STACKIT may deny or remove its listing and integration.
Maturity level
- Products must reach the General Availability (GA) level before listing and full integration into the STACKIT Marketplace. General Availability (GA) means that a product is fully developed, stable, and ready for production use. It has undergone rigorous testing and is officially released for widespread public access and support.
Business suitability
- STACKIT Marketplace products must be suitable for business use. This includes maintaining a professional online presence and providing customer support.
Security standards
- STACKIT Marketplace products must adhere to enterprise security best practices and industry-accepted standards for software security. As a vendor, you are responsible for selecting the specific standards and best practices that are relevant to your product. STACKIT does not predetermine these. You must document the chosen standards and provide this documentation to STACKIT.
- All software components and subcomponents must be free of known security vulnerabilities, spyware, or malicious code of any kind.
Security and vulnerability management
- To ensure security, you are responsible for ensuring that the SaaS application underpinning your STACKIT Marketplace product undergoes annual penetration testing. Qualified independent personnel perform these tests to identify and address security risks, and you must confirm their completion to STACKIT.
- To reduce security risks, perform regular vulnerability checks to detect potential issues. You are responsible for remediating identified vulnerabilities within a defined period, based on their criticality.
- All security-relevant events are logged in a tamper-proof manner. These logs are continuously evaluated to monitor for security threats.
Secure software development
- During software development static application security testing (SAST) must be used to check for vulnerabilities.
- During software development dynamic application security testing (DAST) should be used to check for vulnerabilities.
Secure authentication
- API and (customer) data access for STACKIT Marketplace products must be authenticated and authorized.
- Multi-factor authentication (MFA) is recommended and provided for customers.
- Authentication via a customer-selected Identity Provider (IdP) is supported.
- Authentication data is protected during transmission and storage to prevent unauthorized access.
Data protection
- Communication over public networks must be encrypted, using TLS 1.2 or higher if HTTPS is implemented.
- Persistent customer data for STACKIT Marketplace products must be encrypted at rest at the application level.
- Passwords are stored as salted hashes, using a salt of at least 32 bits.
- All consent related to data processing is logged.
- Data separation is maintained for different processing purposes to ensure privacy and compliance of personal data.
- An appropriate concept for deleting personal data must be in place for any SaaS application that are used to process personal data.
- Functions for erasing, modifying, and providing personal data are available, with the capability to restrict or stop data processing when necessary.
Change and backup procedures
- Changes to the software underlying each STACKIT Marketplace product must be thoroughly tested before deployment.
- Regular backups are performed for each product, with backup media stored in a secure, separate location.
- Backup integrity is verified through recovery tests at least once a year.
System hardening
- Your SaaS application and its dependencies must be hardened according to a policy you define. STACKIT does not predetermine this policy.
However, STACKIT requires adherence to common industry standards. For example, if a CIS Benchmark exists for any component, you should harden that component according to the applicable CIS Benchmark.
You must document your hardening policy and provide this documentation to STACKIT.
Architectural requirements
Section titled “Architectural requirements”Software that is listed and sold on the STACKIT Marketplace must run on the STACKIT Cloud or on the STACKIT infrastructure.
There are certain strategies to fulfill this requirement:
Product runs entirely on STACKIT
Section titled “Product runs entirely on STACKIT”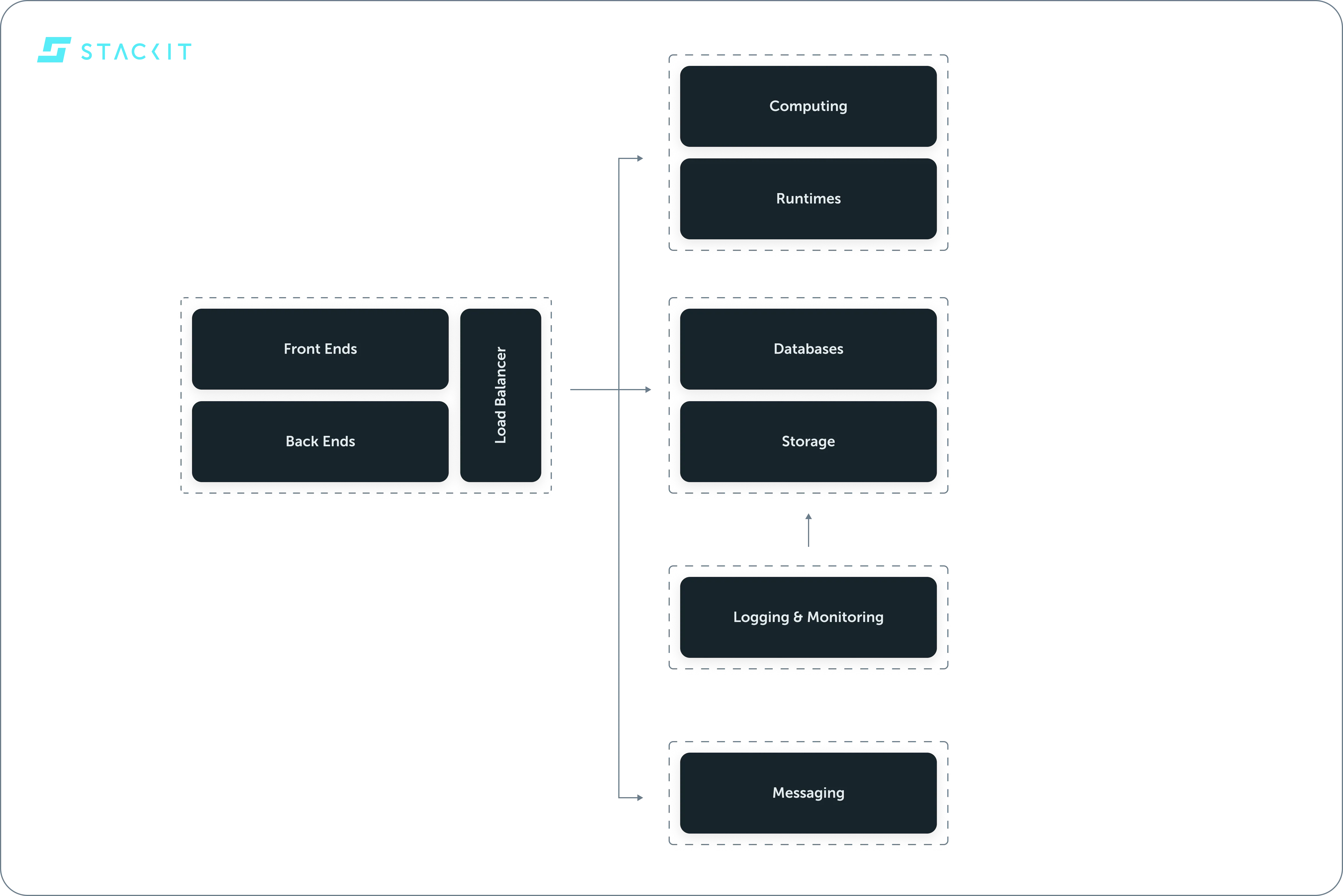
The entire product runs on STACKIT Cloud and STACKIT infrastructure. This includes any supporting (sub-)components.
Product’s data plane runs entirely on STACKIT
Section titled “Product’s data plane runs entirely on STACKIT”
The entire data plane of the product runs on STACKIT Cloud and STACKIT infrastructure. Certain supporting (sub-)components may run on other providers, or on-premise.
Product’s storage incl. storage of any kind must use entirely STACKIT
Section titled “Product’s storage incl. storage of any kind must use entirely STACKIT”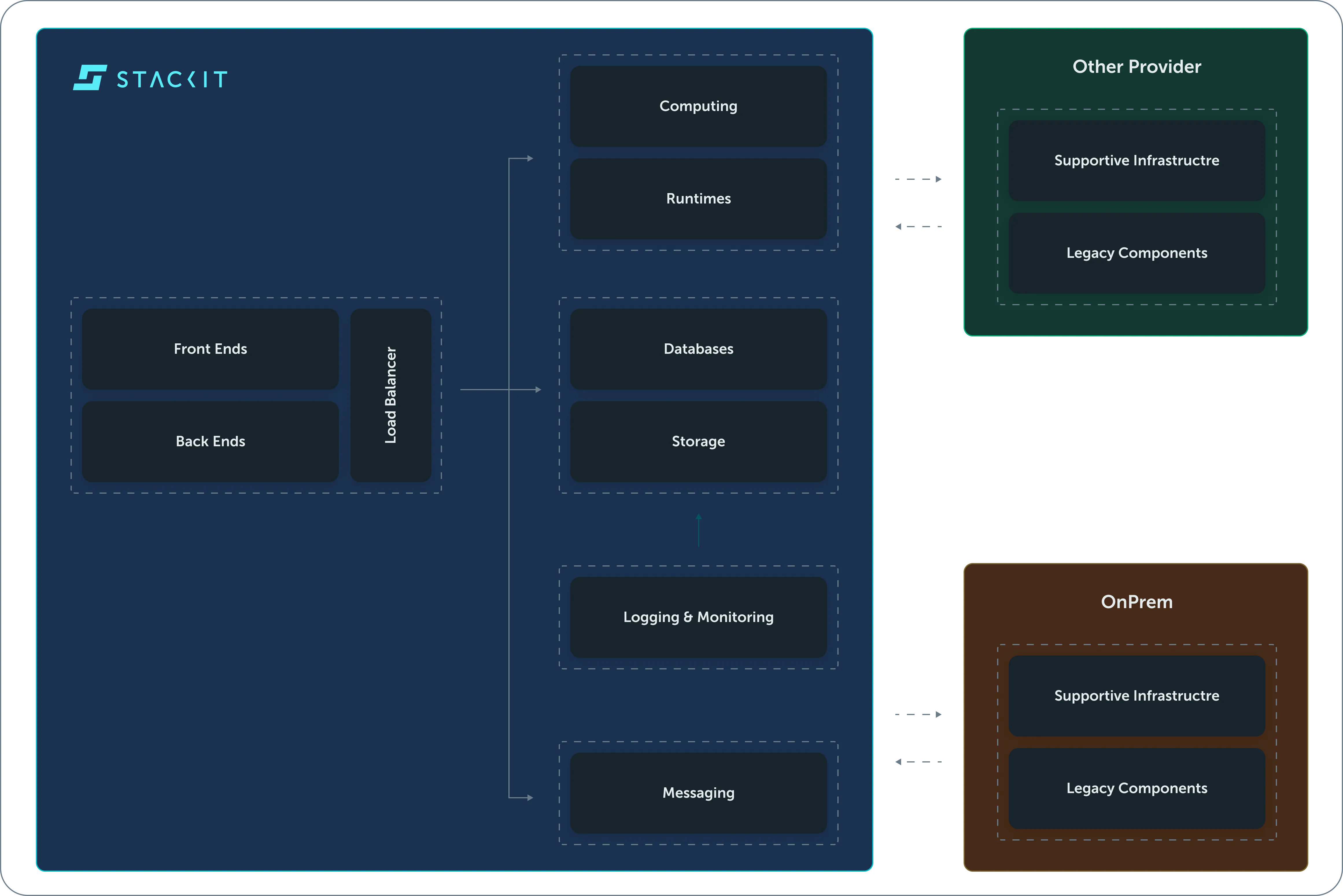
The entire (data) storage must use STACKIT Cloud and infrastructure. This includes any kind of backup, replication, or data recovery, furthermore any kind of user data, including logs, metrics, and traces.